Software Solutions for SAP Environments
CSI tools provides dynamic analytics tools that deliver intelligence from and to decisions taken in access governance for SAP environments. Offered as: On-premise, Software as a Service or Managed Service.
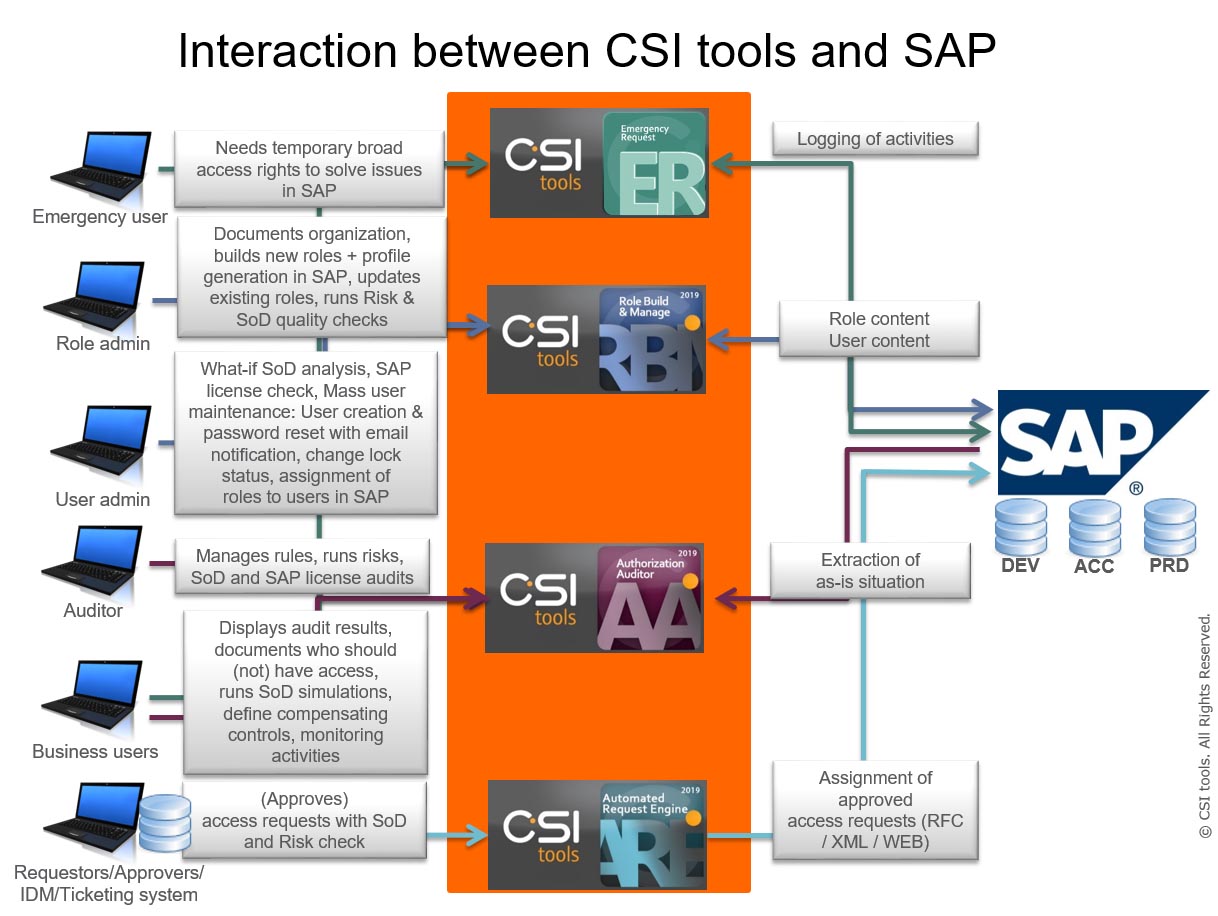
CSI tools' Governance, Risk and Compliance solution for SAP environments enables organizations to manage regulations, compliance and mitigate risks in managing organization’s operations.
The CSI tools GRC Suite:
- helps organizations to automatically detect, manage and prevent access risk violations (incl. Critical access rights and SoD conflicts) and prevents and reduces unauthorized access to company data. Access risk violations, that cannot be prevented by changing access rights, can be mitigated via compensating controls that are documented and monitored via CSI tools.
- eliminates excessive authorizations risks that companies experience with their emergency users.
- manages compliance and policy management. Organizations can manage and monitor their internal control environment, mitigate risks and report the overall state of the compliance activities. It supports the complete life cycle. This helps organizations to reduce the cost of compliance and improve management transparency. CSI tools' GRC Suite enables organizations to develop compliance management processes and policies in their environment.
- assists users to self-service their access requests with approval driven workflows and approval of access. The access requests are handled automatically, so human errors can be avoided and the user administration process wil be more efficient and effective. CSI tools minimizes the time and costs of access risk management.
- builds and maintains SAP roles automatically with correct assignment of non-organizational and organizational values, correct restrictions of functionality while preventing new SoD conflicts. These features allow to check if the role content does not have any inconsistencies.
The NIST framework for SAP Access Security
The NIST Framework explained
The Framework enables all organizations - regardless of size, degree of cybersecurity risk, location (in or outside US) or cybersecurity sophistication - to apply the principles and best practices of risk management to improve the cybersecurity. This can be done by assembling predefined and best-practice standards, guidelines, and practices.
The NIST Framework is a risk-based approach and consists of three parts: The Framework Core, the Framework Profile, and the Framework Implementation Tiers.
The Power of Workflow
The Power of Workflow
Workflow makes life easier: it helps streamlining and automate tasks, minimize rooms for error and will increase efficiency. In processes where multiple persons are involved, like the user provisioning process, implementing a workflow can enhance the efficiency of the whole team.
What are the pros and cons of converting authorization fields to organizational levels?
If business requires, it's possible in SAP to promote non-organizational authorization fields to organizational fields. This can be done using PFCG_ORGFIELD_CREATE. However, upon use it is possible that you receive the message that the program has become obsolete. To counter this, SAP has delivered a new transaction: SUPO/SUPO_SEL (see note 2625102). Once done in DEV, you will need to do this in QAS and PROD, and do the field conversion as well because the conversion is NOT transportable.
Security risks of Robotic Processing Automation (RPA) in SAP
Nowadays we see an increase in Robotic Processing Automation (RPA). RPA is based on executing automated scripts, by software bots. So, RPA can operate in place of a human being and therefore save time and costs.
RPA in SAP comes with risks for data leakage and fraud of the business critical and sensitive data, therefore governance and security is of great importance. This blog gives insight into these security risks and how to tackle them.
Privileged Access Management
SAP systems contains business critical and sensitive data that must be protected. Nowadays we have new challenges regarding the protection of this data. Environments are becoming more and more complex, access is possible via the cloud and the systems are distributed across geographical locations.
The Secure Habits for Securing SAP systems
SAP systems contain business critical, sensitive and personal information that needs to be safeguarded from (cyber) security threats. We listed 7 secure habits that can help you with securing your SAP environment(s).
SAP User Licenses
SAP systems contain critical and sensitive data. Securing this data is essential and, because of SoX and GDPR, we see that implementing security during implementation projects is part of the scope.
Access Certification
Access certification provides the support for process and role owners to collect and manage attestations that users only have the access privileges required to perform their job function. It facilitates faster and accurate access reviews of user privileges by highlighting conflicting permissions in users' access entitlements that have to be revoked or approved under listed exceptions.
Implementing compliancy for SAP environments
SAP systems contain business critical data and needs to be secured. But investing in security means investing time and money. It is always difficult to find a budget for security related tasks. But do note that the costs for non-compliancy like damage to the brand, fines and penalties, theft of proprietary and loss of revenue are way higher than investing in a good solution for compliancy.
Leaflets & Brochures
Get in touch
Pathlock Benelux
Support Direct
Link to the support portal https://support.pathlock.com
To gain access to the new support portal, please contact us at customersupport@pathlock.com
Tel. +32 16 308 008
Address
Kempische Steenweg 303/200
B-3500 Hasselt, Belgium
Via phone
Tel: +32 16 308 000
©1997-2025 Pathlock Benelux. All rights reserved. - Privacy Policy - Cookie Policy - Code of Ethical Conduct - Sitemap